Rootkit Alert
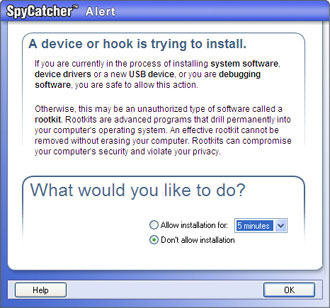
A root kit is a set of tools (programs) used by an intruder after furtively accessing a computer system. These tools can help the attacker maintain access to the system and use it for malicious purposes without being detected.
Typically, a root kit is completely hidden on your computer and often includes software to intercept data from terminals, network connections, and the keyboard. A root kit can also include utilities to help the attacker subsequently access the system more easily.
To respond to this alert:
If you are installing drivers or other software that you trust, choose allow from the drop-down list for as long as you need.
If you are installing new hardware, choose allow from the drop-down list for the time it takes for the installation.
Choose Don't allow installation from the drop-down list in all other cases.
Note: If you have lost functionality, turn off rootkit protection and repeat.